Cisco Meraki MS120-48FP Switch
Cisco Meraki MS120-8 Switch
Cisco Meraki MS125-48FP Switch
Cisco Meraki MS125-24 Switch
Cisco Meraki MS120-48LP Switch
Cisco Meraki MS125-48 Switch
Cisco Meraki MS120-8LP Switch
Cisco Meraki MS125-48LP Switch
Cisco Meraki MS125-24P Switch

Cisco Meraki Z3C LIC-Z3C-ENT-1D Enterprise License and Support-1 Day
P/N: LIC-Z3C-ENT-1DMeraki Z3C Enterprise License and Support-1 Day
Liên hệ ngay
Overview:
The Cisco Meraki Z-Series teleworker gateway is an enterprise class firewall, VPN gateway and router. Each model offers five gigabit ethernet ports and wireless for connectivity. Each model is designed to securely extend the power of Meraki cloud managed networking to employees, IT staff, and executives working from home.
Using Meraki’s proven and highly scalable Auto VPN technology, administrators can deploy network services including VoIP and remote endpoints with automatic, zero-touch provisioning. Additionally the Z series provides secure wired and wireless access, and increases end-user productivity through Layer 7 traffic shaping.
All models feature a high-performance stateful firewall, support for VLANs, inter-VLAN routing, and isolation to segregate corporate data from recreational traffic. The Z3 offers the latest in wireless performance with 802.11ac Wave 2 technology with MU-MIMO support to provide reliable and high speed network access for most demanding business applications and latest devices.
Z-Series and Meraki Cloud Management: A Powerful Combo
All Meraki devices are managed via the Meraki cloud, with an intuitive browser-based interface. Since the Z series is selfconfiguring and managed over the web, you can repidly deploy at remote locations without any assistance from end-users. Meraki Cloud services monitor all devices 24x7 and deliver realtime alerts if any device encounters a problem. Remote diagnostics tools enable real-time troubleshooting through any web browser. New features and enhancements are delivered seamlessly over the web, so you never have to manually download software updates or worry about missing security patches.
Z3C Highlights
Hardware
Wireless
Traffic shaping and application management
|
Teleworker gateway services
Cloud-based centralized management
|
Features:
Auto VPN
Leveraging Meraki’s cloud architecture, VPN tunnels to HQ or the data center can be enabled via a single click without any commandline configurations or multi-step key permission setups. Meraki’s patent-pending Auto VPN technology automatically tunnels, hole punches, sets up route tables, and establishes the IPsec connections, completely eliminating the complexity seen in traditional site-to-site VPN solutions.
Application-aware traffic shaping
The Z-Series includes an integrated layer 7 packet inspection, classification, and control engine, enabling you to set QoS policies based on traffic type. Prioritize your mission critical applications like VoIP or remote desktop, while setting limits on recreational traffic, e.g., peerto-peer and video streaming.
Simple, powerful security from end to end
With end-to-end VPN encryption, corporate data is always protected. Additionally the Meraki Z3 supports 802.1x wired port authentication, offering network and endpoint security no matter where the gateway may be deployed.
Self-configuring, self-optimizing, self-healing
When plugged in, the Z-Series automatically connects to the Meraki cloud, downloads its configuration, and joins your network. In case of WAN IP address changes, the Z-Series self heals by re-establishing the site-to-site VPN tunnels using the new IP address. Also, if a supported 3G/4G modem is connected and primary WAN uplink connectivity fails, the Z-Series will automatically failover to cellular.
Industry-leading cloud management
Meraki’s award-winning cloud management architecture unifies WAN, LAN, and wireless management under a web based dashboard, and scales easily from small deployments to large, multi-site deployments with tens of thousands of devices. The Meraki dashboard provides intuitive yet powerful role-based administration, firmware updates, configuration changes, email alerts, and easy to audit change logs
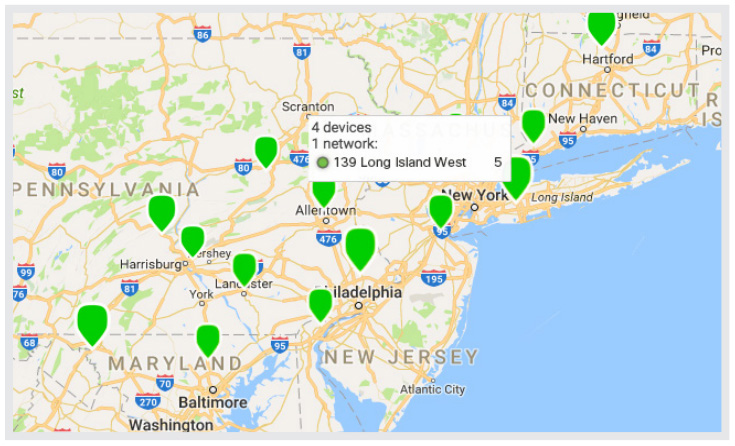
Cloud Management:
Cisco Meraki's cloud based management provides centralized visibility & control over Cisco Meraki's wired & wireless networking hardware, without the cost and complexity of wireless controllers or overlay management systems. Integrated with Cisco Meraki's entire product portfolio, cloud management provides feature rich, scalable, and intuitive centralized management for networks of any size.
Highlights
- Unified visibility and control of the entire network via a single dashboard: wireless, switching, and security appliances
- Streamlines large networks with tens of thousands of endpoints
- Zero-touch provisioning for rapid deployment
- Built-in multi site network management tools
- Automated network monitoring and alerts
- Intuitive interface eliminates costly training or added staff
- Network tagging engine - search and sync settings by tag
- Role-based administration and auditable change logs
- Continuous feature updates delivered from the cloud
- Highly available and secure (PCI / HIPAA compliant)
Cloud Managed Networks
Cisco Meraki's hardware products are built from the ground up for cloud management. As a result, they come out of the box with centralized control, layer 7 device and application visibility, real time web-based diagnostics, monitoring, reporting, and much more.
Cisco Meraki networks deploy quickly and easily, without training or dedicated staff. Moreover, Cisco Meraki provides a rich feature set that provides complete control over devices, users, and applications, allowing for flexible access policies and rich security without added cost or complexity.
Cisco Meraki's cloud management provides the features, security, and scalability for networks of any size. Cisco Meraki scales from small sites to campuses, and even distributed networks with thousands of sites. Cisco Meraki devices, which self-provision via the cloud, can be deployed in branches without IT. Firmware and security signature updates are delivered seamlessly, over the web. With the cloud, branches can automatically establish secure VPN tunnels between one another with a single click.
With a secure, PCI and HIPAA compliant architecture and fault tolerant design that preserves local network functionality during WAN outages, Cisco Meraki is field proven in high security and mission critical network applications.
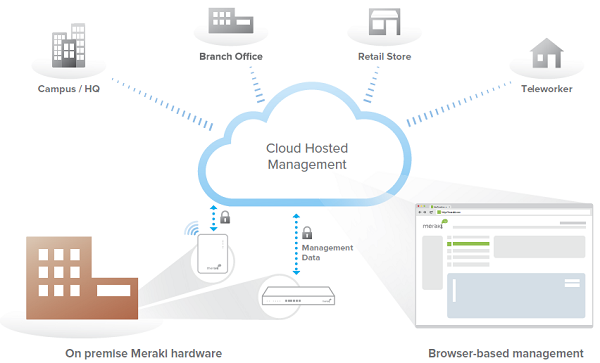
Cloud Management Architecture
Cisco Meraki's architecture provides feature rich network management without on-site management appliances or WiFi controllers.
Every Cisco Meraki device - including wirelesss access points, Ethernet switches, and security appliances - connects over the Internet to Cisco Meraki's datacenters, which run Cisco Meraki's cloud management platform. These connections, secured via SSL, utilize a patented protocol that provides real time visibility and control, yet uses minimal bandwidth overhead (typically 1 kbps or less.)
In place of traditional command-line based network configuration, Cisco Meraki provides a rich web based dashboard, providing visibility and control over up to tens of thousands of Cisco Meraki devices, anywhere in the world. Tools, designed to scale to large and distributed networks, make policy changes, firmware updates, deploying new branches, etc. simple and expedient, regardless of size or location. Cisco Meraki's real time protocols combine the immediacy of on-premise management applications with the simplicity and centralized control of a cloud application.
Every Cisco Meraki device is engineered for cloud management. Specifically, this means that Cisco Meraki devices are designed with memory and CPU resources to perform packet processing, QoS, layer 3-7 security, encryption, etc. at the network edge. As a result, no network traffic passes through the cloud, with the cloud providing management functionality out of the data path. This architecture enables networks to scale horizontally, adding capacity simply by adding more endpoints, without concern for centralized bottlenecks or chokepoints. Equally important, since all packet processing is performed on premise, end-user functionality is not compromised if the network's connection to the cloud is interrupted.
Cisco Meraki's cloud platform is designed to spread computation and storage across independent server clusters in geographically isolated datacenters. Any server or datacenter can fail without affecting customers or the rest of the system. Additionally, Cisco Meraki's datacenter design is field proven to support tens of thousands of endpoints.
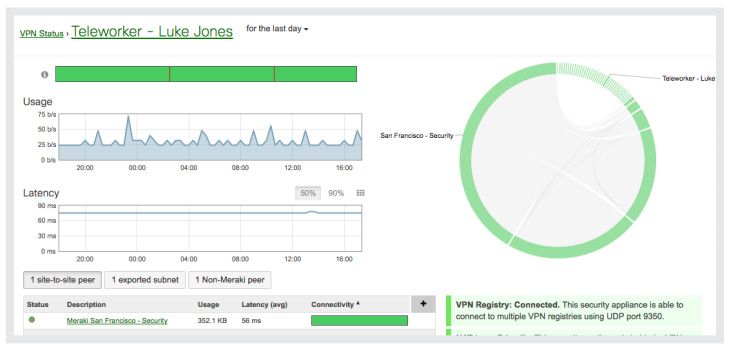
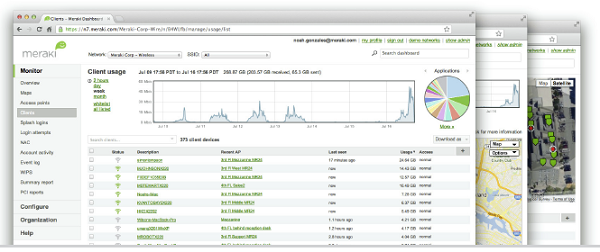
Powerful Insight and Troubleshooting Tools
Cisco Meraki's cloud architecture delivers powerful insight and includes live tools integrated directly into the dashboard, giving instant analysis of performance, connectivity, and more. Using live tools, network administrators no longer need to go on site to perform routine troubleshooting tests. Visibility into devices, users, and applications gives administrators the information needed to enforce security policies and enable the performance needed in today's demanding network environments.
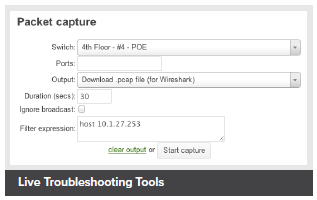
Troubleshooting tools such as ping, traceroute, throughput, and even live packet captures are integrated directly into the Cisco Meraki dashboard, dramatically reducing resolution times and enabling troubleshooting at remote locations without on-site IT staff.
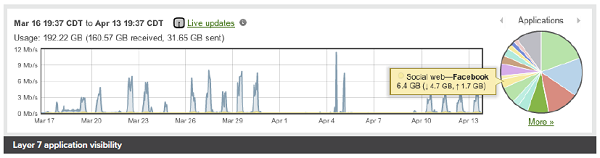
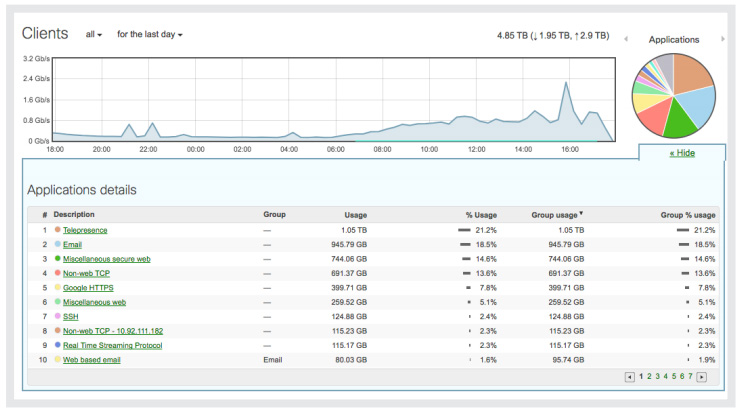
Layer 7 application visibility
|
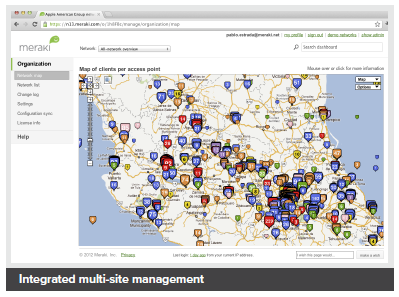
Integrated multi-site management
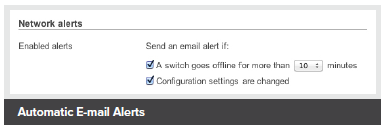
Automatic E-mail Alerts |
Live Troubleshooting Tools
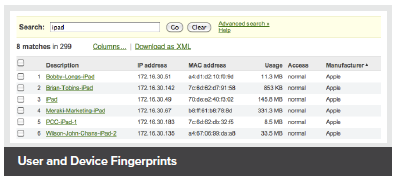
User and Device Fingerprints
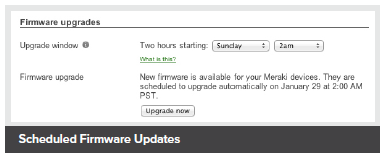
Scheduled Firmware Updates |
Out-of-Band Control Plane
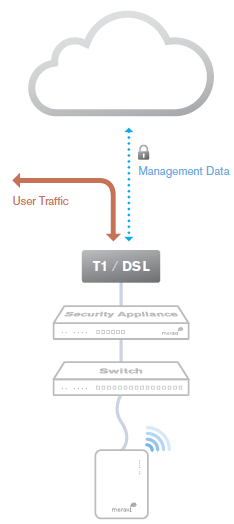
Cisco Meraki's out-of-band control plane separates network management data from user data. Management data (e.g., configuration, statistics, monitoring, etc.) flows from Cisco Meraki devices (wireless access points, switches, and security appliances) to Cisco Meraki's cloud over a secure Internet connection. User data (web browsing, internal applications, etc.) does not flow through the cloud, instead flowing directly to its destination on the LAN or across the WAN.
|
Advantages of an out of band control plane:
What happens if a network loses connectivity to the Cisco Meraki cloud?
While Cisco Meraki's cloud is unreachable, management, monitoring, and hosted services are temporarily unavailable:
|
 |
Cisco Meraki Datacenter Design
Cisco Meraki's cloud management service is colocated in tier-1, SAS70 type II certified datacenters. These datacenters feature state of the art physical and cyber security and highly reliable designs. All Cisco Meraki services are replicated across multiple independent datacenters, so that customer-facing services fail over rapidly in the event of a catastrophic datacenter failure.
Redundancy
Availability Monitoring
Disaster Recovery
Cloud Services Security
Physical Security
|
Out-of-Band Architecture
Disaster Preparedness
Environmental Controls
Certification
Service Level Agreement
|
Security Tools for Administrators
In addition to Cisco Meraki's secure out-of-band architecture and hardened datacenters, Cisco Meraki provides a number of tools for administrators to maximize the security of their network deployments. These tools provide optimal protection, visibility, and control over your Cisco Meraki network.
Two-factor authentication
Two-factor authentication adds an extra layer of security to an organization's network by requiring access to an administrator's phone, in addition to her username and password, in order to log in to Cisco Meraki's cloud services. Cisco Meraki's two factor authentication implementation uses secure, convenient, and cost effective SMS technology: after entering their username and password, an administrator is sent an a one-time passcode via SMS, which they must enter before authentication is complete. In the event that a hacker guesses or learns an administrator's password, she still will not be able to access the organization's account, as the hacker does not have the administrator's phone. Cisco Meraki includes two-factor authentication for all enterprise users at no additional cost.
Password policies
Organization-wide security policies for Cisco Meraki accounts help protect access to the Cisco Meraki dashboard. These tools allow administrators to:
- Force periodic password changes (e.g., every 90 days)
- Require minimum password length and complexity
- Lock users out after repeated failed login attempts
- Disallow password reuse
- Restrict logins by IP address
Role-based administration
Role-based administration lets supervisors appoint administrators for specific subsets of an organization, and specify whether they have read-only access to reports and troubleshooting tools, administer managed guest access, or can make configuration changes to the network. This minimizes the chance of accidental or malicious misconfiguration, and restricts errors to isolated parts of the network.
Configuration change alerts
The Cisco Meraki system can automatically send human-readable email and text message alerts when configuration changes are made, enabling the entire IT organization to stay abreast of new policies. Change alerts are particularly important with large or distributed IT organizations.
Configuration and login audits
Cisco Meraki logs the time, IP, and approximate location (city, state) of logged in administrators. A searchable configuration change log indicates what configuration changes were made, who they were made by, and which part of the organization the change occurred in.
SSL certificates
Cisco Meraki accounts can only be accessed via https, ensuring that all communication between an administrator's browser and Cisco Meraki's cloud services is encrypted.
Idle Timeout
30 seconds before being logged out, users are shown a notice that allows them to extend their session. Once time expires, users are asked to log in again.
Specifications:
|
Interfaces
Network and Security Services
Integrated Wireless
Monitoring and Reporting
Remote Diagnostics
|
WAN Performance Management
Management
Performance
Physical and Environmental Specifications
Regulatory
Warranty
|
License Editions:
An organization must have a valid Enterprise Edition license or Advanced Security Edition license for the MX series in order to work properly. Each organization is licensed for a maximum number of security appliances for a certain amount of time (typically from one year to five years).
In addition, each organization is required to use either the Enterprise Edition or the Advanced Security Edition uniformly. For example, you can have all 25 appliances using Enterprise Edition or Advanced Security Edition, but you cannot have 20 appliances using one edition and 5 using the other edition. If you wish to use Enterprise Edition for some appliances and Advanced Security Edition for other appliances, you need to create two organizations, one for your appliances with the Enterprise Edition, and another for the appliances with the Advanced Security Edition.
You can manage a given organization's licenses on the Organization > License info page. The page displays the following information:
- Status: OK or problem
- Expiration date
- MX Advanced Security Enabled or Disabled
- Licensed device limit for each device type
- Current device count for each device type
- License history (list of licenses that have been applied to the network)
Enterprise vs. Advance Security license
The following table provides a list of the major features and the required licensing.
| Stateful firewall | Enterprise license | Advanced Security license |
| VLAN to VLAN routing |
√
|
√
|
| Link bonding / failover |
√
|
√
|
| 3G / 4G failover |
√
|
√
|
| Traffic shaping / prioritization |
√
|
√
|
| WAN optimization |
√
|
√
|
| Site-to-site VPN |
√
|
√
|
| Client VPN |
√
|
√
|
| MPLS to VPN Failover |
√
|
√
|
| Splash pages |
√
|
√
|
| Configuration templates |
√
|
√
|
| HTTP content caching |
√
|
√
|
| Group Policies |
√
|
√
|
| Client connectivity alerts |
√
|
√
|
| Intrusion detection / prevention |
|
√
|
| Content filtering |
|
√
|
| Anti-virus and anti-phishing |
|
√
|
| Youtube for Schools |
|
√
|
| Web Search Filtering |
|
√
|
Adding licenses
You can add a license by clicking Add another license. You will then have two actions, or "operations", to choose from:
- License more devices: increases the number of devices that can exist within this Cisco Meraki Dashboard organization.
- Renew my Dashboard license: extends the licensing period of this Cisco Meraki Dashboard organization. You must renew the license for all devices in the organization. You cannot renew licensing for only certain devices within the organization.
You cannot add an Enterprise MX license to an Advanced Security organization. Adding an Advanced Security license to an Enterprise organization will convert that organization to Advanced Security. All existing Enterprise MX licenses will have their duration halved to compensate for the difference in the licensing costs, and the organization's license cotermination date will be adjusted accordingly.
Expired licenses or exceeding the licensed device limit
If an organization's license is expired or the number of devices in the organization exceeds the licensed limit, the administrator has 30 days to return the organization to a valid licensed state. During this grace period, the system reminds the administrator to add additional licenses. After 30 days, administrators are not able to access the Dashboard (except to add additional licenses) and all Cisco Meraki equipment in the organization will cease to function.
| Cloud Managed Security Appliance | |
| Z3C-HW-WW | Meraki Z3C LTE Teleworker Gateway *Please Note: Cisco Meraki Enterprise license purchase required for each Gateway. |
| Cisco Meraki Enterprise License and Renewal License | |
| LIC-Z3C-ENT-1YR | Cisco Meraki Z3C Enterprise License and Support, 1 Year Enterprise License and Support |
| LIC-Z3C-ENT-3YR | Cisco Meraki Z3C Enterprise License and Support, 3 Year Enterprise License and Support |
| LIC-Z3C-ENT-5YR | Cisco Meraki Z3C Enterprise License and Support, 5 Year Enterprise License and Support |
| LIC-Z3C-ENT-7YR | Cisco Meraki Z3C Enterprise License and Support, 7 Year Enterprise License and Support |
| LIC-Z3C-ENT-10YR | Cisco Meraki Z3C Enterprise License and Support, 10 Year Enterprise License and Support |
| Cisco Meraki Accessories | |
| MA-STND-1 | Cisco Meraki Z3 Vertical Desktop Stand |
| MA-PWR-CORD-US | Cisco Meraki Power cord (US) for MX64, MX65, MX67, MX68, MX84, MX100, MX250, MX450, Z3, Z3C and All MS series switches |
Sản phẩm xem thêm
Cisco Meraki Z3 Series
Cisco Meraki Z3C Series
Chủ sở hữu Website http://thietbicisco.vn/ thuộc về:
CÔNG TY TRÁCH NHIỆM HỮU HẠN THƯƠNG MẠI DỊCH VỤ KẾT NỐI MẠNG
Tên quốc tế: KET NOI MANG SERVICE TRADING COMPANY LIMITED
Tên viết tắt: KET NOI MANG SERVICE TRADING CO.,LTD
Số chứng nhận ĐKKD: 0314815571
Ngày cấp: 03/01/2018, nơi cấp: Sở KH & ĐT TPHCM
Người đại diện: VĂN NHẬT TÂN
Địa chỉ: Số 36/34 Đường Nguyễn Gia Trí, Phường 25, Quận Bình Thạnh, Thành phố Hồ Chí Minh, Việt Nam
Địa chỉ giao dịch: 1061 Phạm Văn Đồng, Phường Linh Tây, Thành Phố Thủ Đức, Thành phố Hồ Chí Minh, Việt Nam
Điện thoại: 84.028.35125568
Hotline: 09 014 014 86
Website: http://ketnoimang.vn | http://thietbifortinet.vn | http://thietbicisco.vn | http://knmrack.vn
Email: sales@ketnoimang.vn